
Procedural
Requirements
Effective Date: April 19, 2022
Expiration Date: April 19, 2027

|
NASA Procedural Requirements |
NPR 8000.4C Effective Date: April 19, 2022 Expiration Date: April 19, 2027 |
| | TOC | Preface | Chapter1 | Chapter2 | Chapter3 | AppendixA | AppendixB | AppendixC | AppendixD | AppendixE | ALL | |
C.1 General Considerations
As implied by their definitions (see Appendix A) risk in the domains of Physical Security and Cybersecurity (PS&C) has the unique characteristic of being often associated with intentional acts of aggression carried out by an "hostile agent" - i.e., an ill-intentioned individual, entity, or even foreign government - against the assets or activities of the affected organization. This may occur in the context of a covert operations, such as the infiltration of a computer system by hackers who intend to take control of its stored information, or of more overt attacks, such as the attempt by a terrorist group to inflict damage to the physical facilities of an organization.
C.2 PS&C Risk Modeling
Despite the above specific characteristic of being often associated with the acts of an hostile human agent (or multiple coordinated agents), PS&C risk scenarios do not differ from any other risk scenarios, in the fact that their progression is still determined by sequences of concatenated events. Accordingly, they can still be represented and described by means of the same types of logic models that are used for other types of risk scenario; however, as further explained below, the "intentional act" characteristics of PS&C risks suggests for their qualitative or quantitative assessment an approach that differs from that customarily applied for most other risks.
In general, detailed representation of complex risk scenario situations may require the use of combinations of different models (e.g., a combination of event trees and fault trees, such as often done in PRA (Probabilistic Risk Assessment). However, for the purposes of the discussion in this Appendix, it is sufficient to refer to a simple conceptual model that corresponds to the "risk statement" descriptions of risk recommended by the NASA RM Handbook [E20].
Per [E20], a risk statement takes the form shown in the below indented paragraph:
GENERIC RISK STATEMENT:
"Given that [CONDITION], there is a possibility of [DEPARTURE] from the baseline adversely impacting [ASSET], thereby leading to [CONSEQUENCE]."
In logic model terms, the above risk statement can be translated into a simple Event Sequence Diagram (ESD) format, as illustrated by Figure C1 below. While a real scenario can be complex and typically include multiple relevant events and/or conditions, at the conceptual level such events can always be grouped into the basic blocks identified in the above generic form of a risk statement, and in the corresponding ESD shown in Fig. C1.
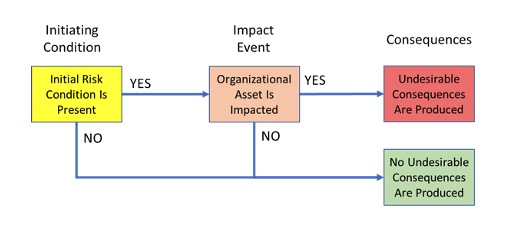
Figure C1 – ESD rendition of a “standard” generic risk statement
For the case of a PS&C risk involving a human hostile agent, the risk statement and corresponding ESD model would take the more specific forms shown, respectively, by the following indented paragraph and by Figure C2:
RISK STATEMENT FOR PS&C RISK INVOLVING HOSTILE:
"Given that [HOSTILE AGENT IS PRESENT], there is a possibility of [BREACH OF SECURITY] from the baseline adversely impacting [ASSET], thereby leading to [CONSEQUENCE]."
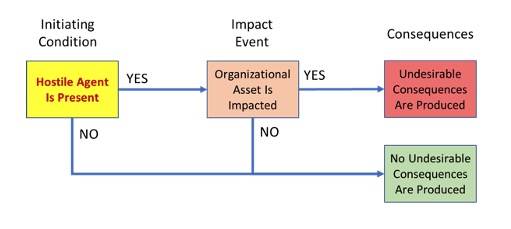
Figure C2 - ESD rendition of a risk statement for PS&C risk involving an hostile agent
The above considerations provide the basis for introducing the concepts of "conditional likelihood" and "conditional risk," as metrics relevant to the evaluation of PS&C domain risk. These concepts directly follow from the general formula that can be used to calculate the likelihood metric as a standard component in the classic risk-metric-duo, i.e., likelihood and consequence severity. When referred to a risk scenario defined in one of the above formats, such a formula is as shown below:
| Likelihood = P(IC) x P(IE | IC), | (Eqn.C1); | |||
| where: | ||||
| IC | = | Initiating Condition | ||
| IE | = | Impact Event | ||
| P(IC) | = | probability of Initiating Event | ||
| P(IE | IC) | = | conditional probability of Impact Event, given the Initiating Condition is present |
||
In the representation of risk resulting from random events, "Likelihood" is the probability that a full scenario sequence, from source to consequences, will occur. Its assessment accounts for the frequency of the scenario and the timeframe in which the scenario can occur. For some purposes, it can be assessed qualitatively. For other purposes, it is quantified in terms of frequency or probability. A complete assessment of likelihood also calls for characterization of its uncertainty.
In the representation of risk resulting from intentional actions by an hostile agent (e.g., a type of intentional cybersecurity threat posed by a specific type of adversary), a quantification or even a qualitative classification (e.g., "high," "low," etc.) of the frequency or probability of such actions may be difficult to produce with sufficient degree of confidence. In such cases, the "Conditional Likelihood" of the portion of the scenario that follows the scenario Initiating Condition "Hostile Agent Is Present" (shown in Fig. C2) corresponds to the component P(IE ??IC) of Eqn.C1. This component is referred to as a "Conditional Likelihood," rather than "Conditional Probability," to indicate that it may be estimated and expressed in qualitative, rather than fully quantitative terms, if this is appropriate and sufficient for risk evaluation purposes. The term "Conditional Probability" may be interchangeably used for such a metric, when it is expressed in fully quantitative terms.
It follows from the above that the Conditional Likelihood (or Conditional Probability) metric, P(IE ??IC) in Eqn.C1, represents the likelihood that, if an intentional threat identified as the risk scenario Initiating Condition (i.e., "Hostile Agent" in the Fig. C2 example) is assumed to be present, such a threat will be successful in producing the scenario consequences. It should be further noted that assuming the Initiating Condition as being present is equivalent, in quantitative terms, to assuming that its probability, P(IC) in Eqn.C1, is equal to 1.
C.2.1 PS&C Risk Modeling for Realistic Multi-Event Scenarios
When a realistic risk representation includes multiple concatenated events, as may be necessary for more complex scenarios, the Conditional Likelihood evaluation still requires considering the scenario as being composed of two conditionally linked primary blocks of events, which will be referred here as Event Block A (EB-A) and Event Block B (EB-B).
In this type of overall scenario sequence, EB-A will represent the risk Initiating Condition constituted by the event, or group of events, willfully caused to occur by an intentional cybersecurity threat, or other type of intentional hostile action against a system.
EB-B, the block of events conditionally following EB-A and only possible if all events in the latter have actually occurred, will instead represent the possible failure of the specifically engineered, or otherwise naturally present defenses that may protect the system of concern from the effects of EB-A.
The considerations made above for the simplified scenario representations and formulations given by Figs. C1 and C2, and by Eqn.C1 remain valid when the individual scenario components IC and IE are replaced by the corresponding "event blocks," EB-A and EB-B.
C.3 PS&C Risk Evaluation
Per the discussion presented above in C.2, for PS&C risks affecting a given system and involving as their Initiating Condition a specific type of assumed intentional threat to that system, the risk evaluation can be based on a modified risk-metric-duo that will include, besides the customary Consequence Severity metric, a Conditional Likelihood metric as a replacement of the (unconditional) Likelihood metric used for all the other non-intentionally-initiated risk scenarios.
The modified duo constituted by the Conditional Likelihood and Consequence Severity metrics therefore expresses a "Conditional Risk" level for a system of concern, given an intentional threat / "Hostile Agent" which is assumed present. For a given system, a set of Conditional Risks will usually be assumed if the corresponding intentional / Hostile Agent threats are deemed possible and credible.
While in theory Initiating Conditions involving intentional threats can be evaluated / assessed via probability / likelihood estimation, the variability of the underlying driving factors (e.g., political conditions, conflict conditions, etc.) can make such assessments difficult to execute with confidence and unreliable over time. The Conditional Risk evaluation approach sidesteps these difficulties. The possible EB-A Initiating Condition types can be prioritized within the PS&C risk approach framework by qualitative relevance ratings - e. g., as per inputs from intelligence agencies, updated at regular time intervals to reflect the evolving driving factors, while the correspondingly identified EB-B events and factors can be evaluated using standard logic-probabilistic models and estimations, to assess the probability that the affected system or mission may be compromised by each type of intentional threat in the prioritized PS&C threat list, if such a threat is assumed to be present and active against the system.
C.3.1 Potential Vulnerability and Control Effectiveness in PS&C Risk Scenarios
The conditional likelihood of system compromise (the Impact Event, or EB-B in the above discussions), given a certain specified type of threat being present and active (Initiating Condition or EB-A in those same discussions), is a measure of the system "Potential Vulnerability" to that type of threat.
The attribute "potential" is used in the term Potential Vulnerability to differentiate it from the deterministic, definitions of "vulnerability" that can be found in cybersecurity lexicons, whereby, by stating that a vulnerability to a certain type of threat exists in a given system, it is meant that such a system is completely unprotected from that type of threat and certain to be compromised if the threat materializes. Potential Vulnerability, as used in this NPR document, indicates instead a degree of vulnerability to an assumed type of threat, which can be expressed in Conditional Likelihood or Conditional Probability terms.
As an illustration of the concept, consider a network which is assessed as having a 50% conditional probability (or, qualitatively speaking, a "high" conditional likelihood) of unauthorized access to sensitive data, if an attacker sends phishing emails to its authorized user. It would then be reasonable to characterize such a network as having "high potential vulnerability" to phishing attacks.
In certain PS&C risk situations, the Conditional Risk evaluation may assess that a given system has significant degree of Potential Vulnerability to credible threats. In such situations, the development of realistic logic-probabilistic models of the factors that determine the conditional probability of the "EB-B" portions of the associated risk scenarios provides the means for identifying the risk control provisions that can be implemented to reduce the system potential vulnerabilities and cybersecurity risks. The reduction in system Potential Vulnerability produced by the application of a risk control, or set of controls, is a measure of the Control Effectiveness of that control or control-set.
C.3.2 Assessment of PS&C Aggregate Risk
When considering risk produced by intentional threat sources, such as cyber-risk, the representation and assessment of aggregate risk, i.e., the ensemble of credible individual risks of the PS&C intentional-threat kind, will not be feasible in traditional form, since the corresponding scenarios are only partially quantifiable (e.g., via "Conditional Likelihood" or "(Conditional) Potential Vulnerability" metrics as suggested above).
For such cases and associated scenarios, surrogate aggregate risk indices can still be formulated, if this is still considered useful for specific purposes, by substituting threat weights (e.g., reflecting expert judgment supported by relevant and timely sources of information, such as intelligence input) in place of the initiating threat frequency or probability measures that would be used for all other more traditional and common types of risks and scenarios.
| TOC | Preface | Chapter1 | Chapter2 | Chapter3 | AppendixA | AppendixB | AppendixC | AppendixD | AppendixE | ALL | |
| | NODIS Library | Program Management(8000s) | Search | |
This document does not bind the public, except as authorized by law or as incorporated into a contract. This document is uncontrolled when printed. Check the NASA Online Directives Information System (NODIS) Library to verify that this is the correct version before use: https://nodis3.gsfc.nasa.gov.